Recently I had a deeper encounter with Ransomware a form of malware that’s spreading at an alarming rate. It works by restricting the users computer or data then demands that they pay a ransom in order to gain access back. While it's not a new thing creators seem to be bypassing even some of the more advanced virus scanners which offer out of the box web & download scanning.
In 2015 alone the FBI received at least 2,500 complaints related to ransomware attacks, which amounted to approximately $24 million in losses to the victims. Australians have reportedly lost millions from similar forms of malware and online scams this year alone.
This form of malware is commonly spread via phishing emails. These emails appear to come from legitimate companies, luring you to click a link which then offers a website that "appears to be" correct. Visually the site could look identical but it's really a fake, the easiest thing to-do is compare web addresses. Real site VS the fake "http://auspost.com.au/" isn't the same as "http://auspost-1f290.rnd.net.au".
My mother had unintentionally downloaded and opened a self executing zip file even with my rants about opening certain emails, files and NOD32 being installed. "Crypt0Locker" was still downloaded and ran. The program copied itself to a few locations while encrypting or at least obfuscating the source of files and then adding the file extension ".encrypted".
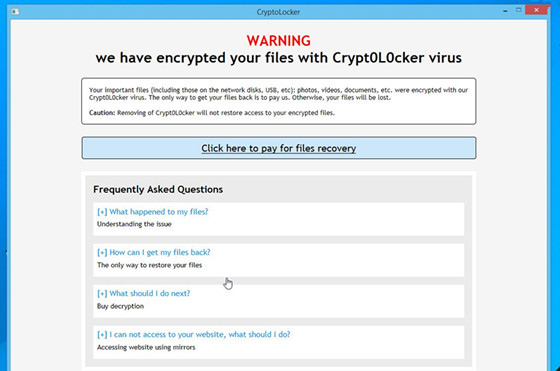 A browser window appeared with instructions on what had just happened and how to gain control of the files again.
A browser window appeared with instructions on what had just happened and how to gain control of the files again.
The instructions state to deposit X amount of bit coins into a specific address.
The site being served is using the Tor network along with the crypto-currency Bitcoin, unfortunately this makes it a lot harder for law enforcement to track and and put a stop to these malicious people.
So to pay the money or attempt a fix myself? Of-course I went with fix it myself which lead to several hours of research, trial and error then repeat.
The Quickest Fix
A handy feature known as System Restore can resolve this. Unfortunately the feature isn't always on or a restore point is a long time ago. If you're one of the lucky ones you may have a restore point that's recent you can follow the instruction on the Microsoft website to-do this.
The Alternate Fix
First you'll want to remove any traces of the malware to prevent re-infection or at the very least prevent the window from constantly popping up in your face.
The easiest solution is to use a free trial of Malware Bytes or Hitman Pro let one of these scan your entire system and follow the prompts.
Next is attempting to restore files. Shadow Explorer may allow you to see versions of files which could allow restoration. Unfortunately this is a bit of a manual process.
Bleeping Computer provide a very default walkthrough on how to use Shadow Explorer - http://www.bleepingcomputer.com/virus-removal/cryptolocker-ransomware-information#shadow
Prevention
Even the most careful get hit at some stage so the key is educating yourself even if it's a little, try following some of the points below:
- Use a Virus Scanner and keep it up-to date
- Don't open emails unless you're 100% certain it's safe. If the Email Spam filter didn't pick it up then you can examine the From address to check the legitimacy.
- Download files from websites that are being served from the correct Web Address
- Use more modern and secure browsers such as Firefox or Google Chrome
TL;DR - A new version of Crypt0Locker and variations exist where no easy fix is available. The older version of Crypt0Locker had a method to restore files and remove the malware.
You could have a variation of the virus, so these steps may not work for you. To be precise on what actions should be taken you can upload an infected file to this site: https://id-ransomware.malwarehunterteam.com/ which will detect the form of ransomware you've been hit with.
Finally keep an eye on Scamwatch - https://www.scamwatch.gov.au/
